UBC researchers find ways to hackproof smart meters
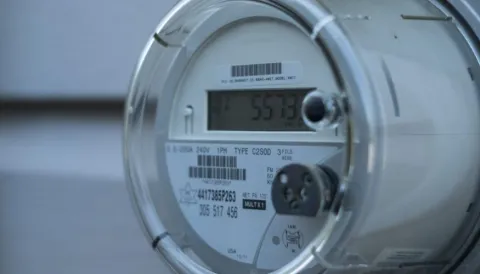
Smart electricity meters are useful because they allow energy utilities to efficiently track energy use and allocate energy production. But because they’re connected to a grid, they can also serve as back doors for malicious hackers. In this Q&A, cybersecurity researcher Karthik Pattabiraman, an associate professor of electrical and computer engineering at UBC, talks about his recent breakthrough aimed at improving the security of these devices and boosting security in the smart grid.
Why is it so important to secure smart meters?
Smart meters are critical components of the smart grid, sometimes called the Internet of Things, with more than 588 million units projected to be installed worldwide by 2022.
In a single household you can have multiple smart devices connected to electricity through a smart meter. If someone took over that meter, they could deactivate your alarm system, see how much energy you’re using, or rack up your bill. In 2009, to cite one real-life example, a massive hack of smart meters in Puerto Rico led to widespread power thefts and numerous fraudulent bills.
Hacked meters can even cause house fires and explosions or even a widespread blackout. Unlike remote servers, smart meters can be relatively easily accessed by attackers, so each smart meter must be quite hackproof and resilient in the field.
How did you approach this problem?
Smart meters are vulnerable to what we call software-interference attacks, where the attacker physically accesses the meter and modifies its communication interfaces or reboots it. As a result, the meter is unable to send data to the grid, or it keeps sending data when it shouldn’t or performs other actions it wouldn’t normally do.
My PhD student and I developed an automated program that uses two detection methods for these types of attacks. First, we created a virtual model of the smart meter and represented how attacks can be carried out against it. This is what we call design-level analysis. Second, we performed code-level analysis. That means probing the smart meter’s code for vulnerabilities, launching a variety of attacks on these vulnerabilities.
Although both techniques successfully discovered attacks against the system, code-level analysis was both more efficient and more accurate than design-level analysis. Code-level analysis found nine different types of attacks within an hour, while design-level analysis found only three.
All of the attacks can be carried out by an attacker with relatively low cost-equipment purchased for less than $50 online, and do not require specialized expertise.
How do your findings improve smart meter security?
Vendors can use the findings to test their designs before they are manufactured, so they can build in security from the get-go. This can make smart meters much harder to crack. By using both approaches—design-level and code-level—you can guard against software tampering on two different fronts.
Our findings can be applied to other kinds of devices connected to a smart grid as well, and that’s important because our homes and offices are increasingly more interconnected through our devices.
Like all security techniques, there is no such thing as 100 per cent protection. Security is a cat-and-mouse game between the attacker and the defender, and our goal is to make it more difficult to launch the attacks. I believe the fact that our techniques were able to find not just one or two vulnerabilities, but a whole series of them, makes them a great starting point for defending against attacks.
Contact
Lou Corpuz-Bosshart
UBC Media Relations
Tel: 604-822-2048
Cel: 604-999-0473
Email: lou.bosshart@ubc.ca